Optionally, with every node or SD-WAN network, access to network intelligence and site analytics.
Giving you full transparency into what’s happening on the network. Local deep packet network monitoring coupled with cloud-based analytics to deliver exceptional, business-driven data.
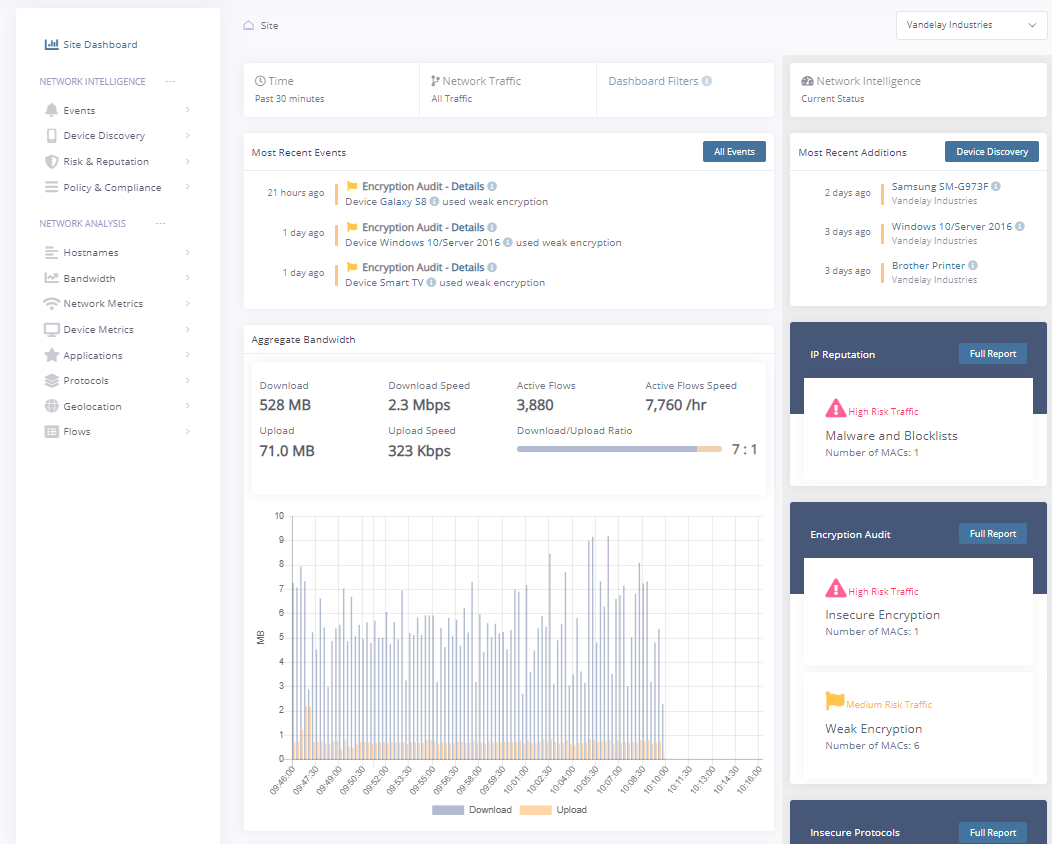
Fusion provides complete visibility and analysis of the traffic flows on an organization’s networks. Using AI-driven network intelligence, clients benefit from reduced cybersecurity risk, data-driven decision making, increased productivity and effective regulatory compliance.
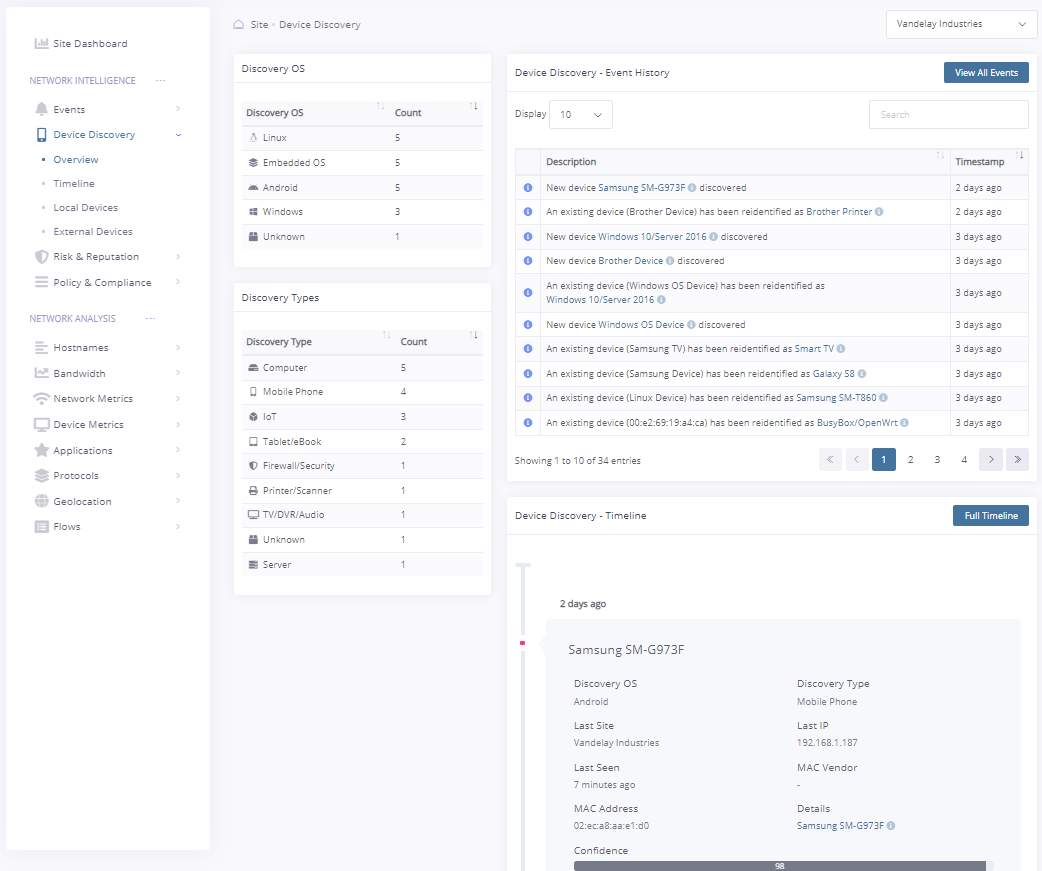
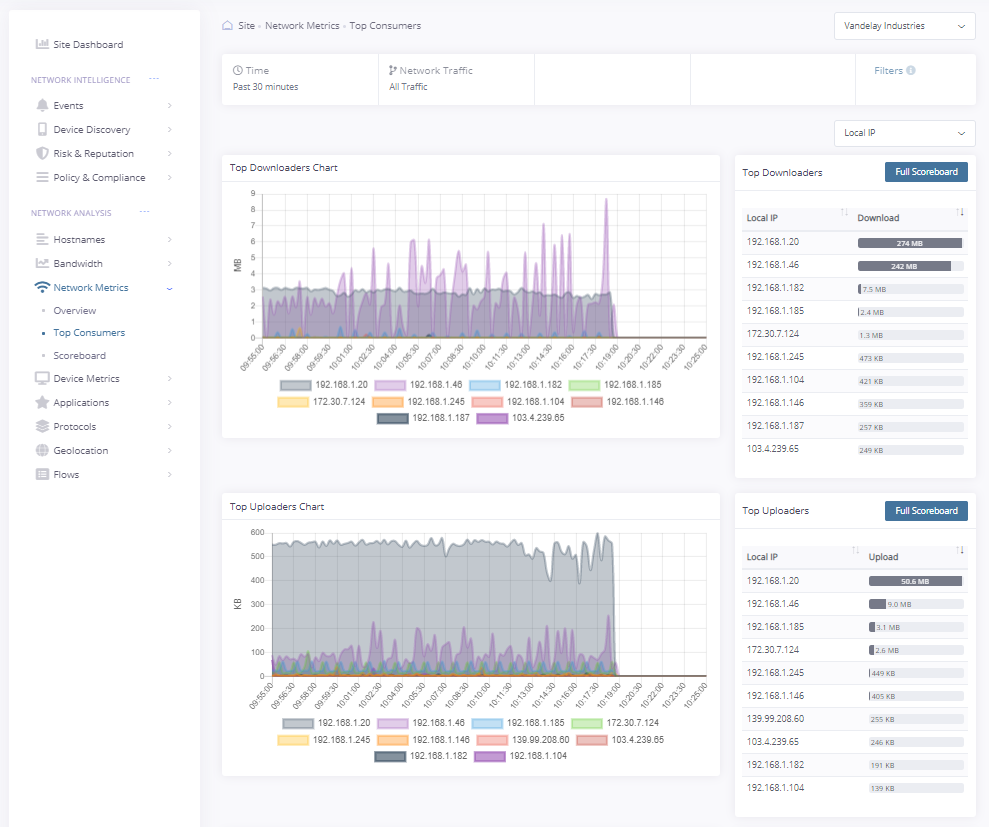
Device Discovery and Top Consumers
The Fusion agent tracks and automatically adds any new devices found on the local network for classification, association and labelling.
-Real-time device discovery and alerting
-Automatic classification of device type using packet analysis
-User-provided data is 100% private, encrypted with a passphrase known only to users
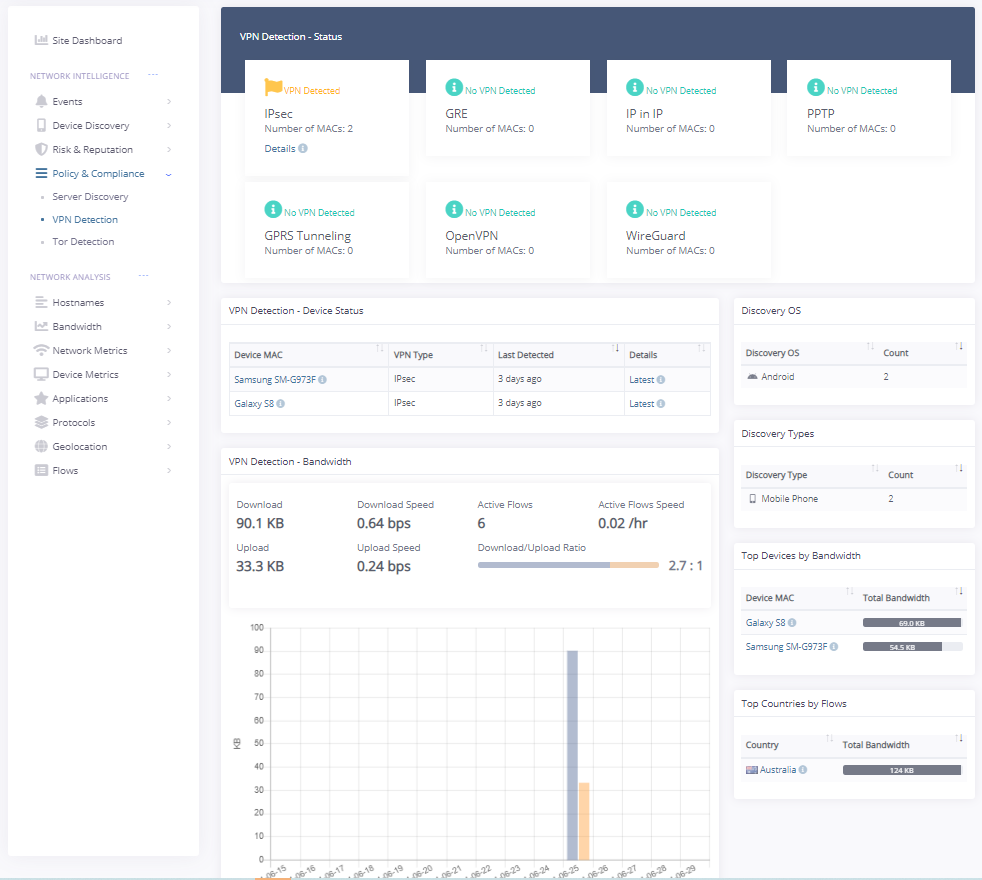
Risk and Reputation
The Fusion machine learning engine is continually analysing network flows and devices on the network to identity threats and risky behaviour.
-Alert and educate team-members
-Reduce cybersecurity risk
-Continuous analysis beyond point-in-time retroactively scans for malicious content.
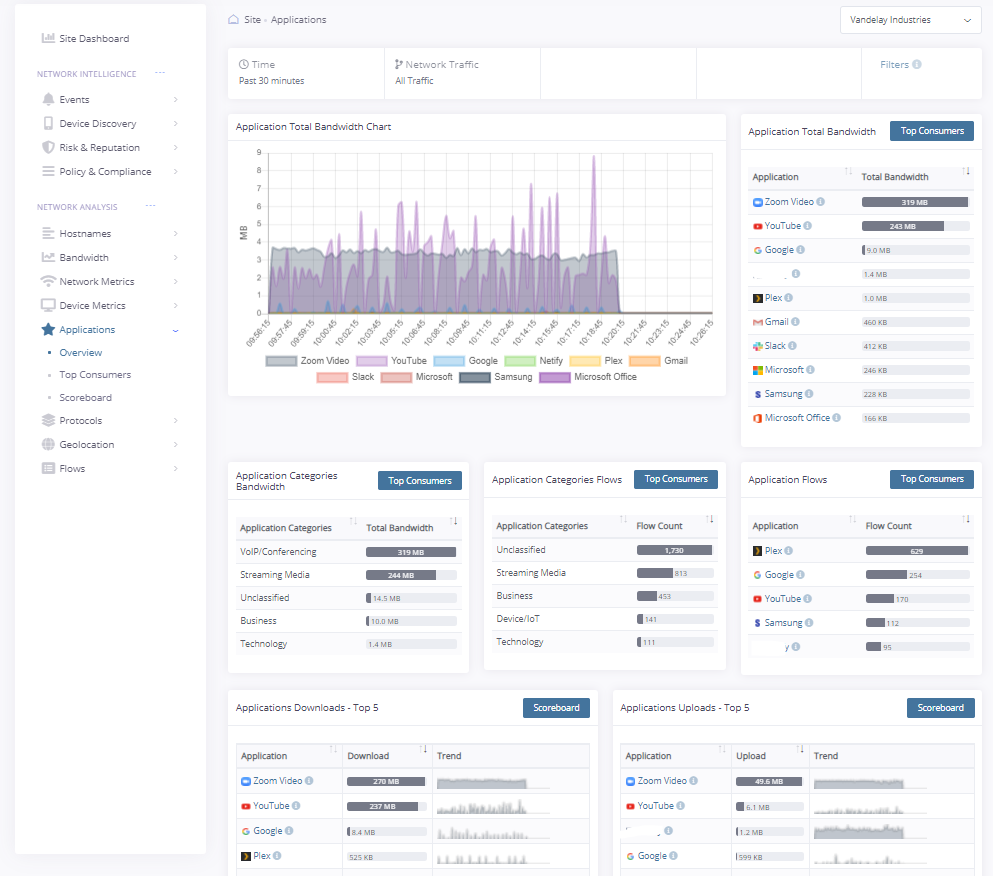
Application Detection
The Fusion machine learning engine and deep packet inspection engine is able to identify applications in use on the network.
-Map flows to an application – including encrypted traffic
-Historical archiving of employee or team-members activity on the network to help solve productivity or policy issues
-Fusion maintains a dynamic list of application signatures
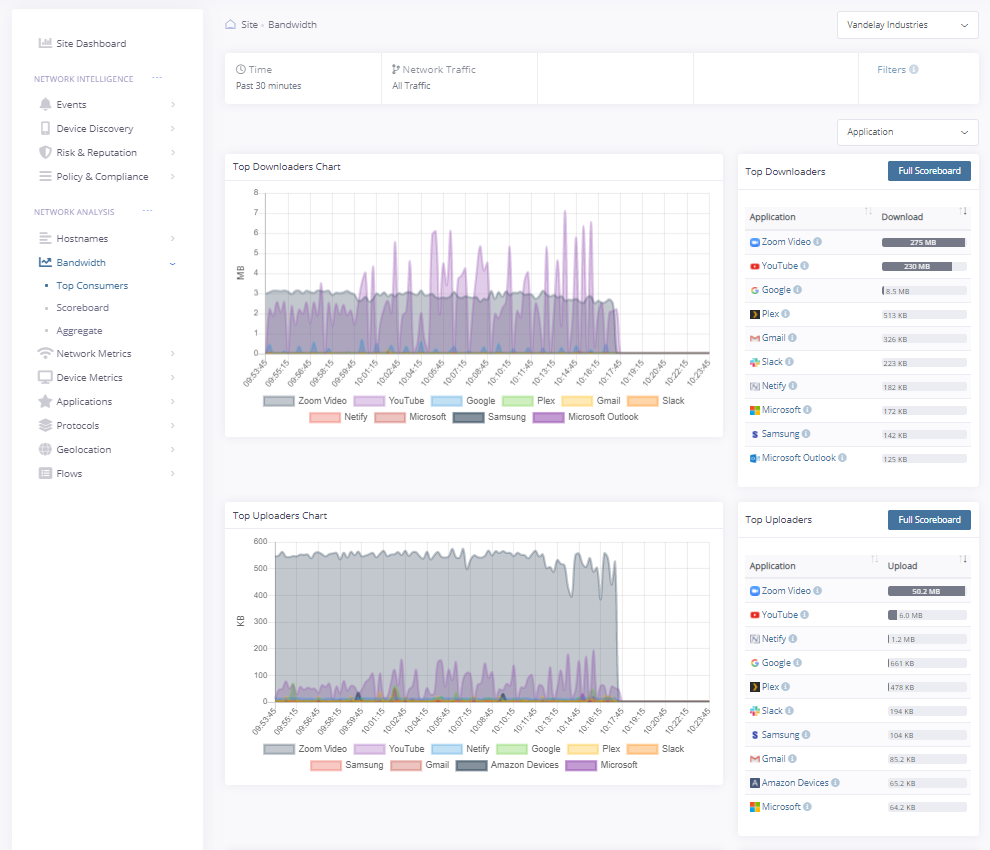
Bandwidth Monitoring
Is a VoIP call suddenly breaking up or video stalling? Find out instantly what devices on the network are increasing latency and consuming bandwidth.
-Identify users/devices consuming the most bandwidth
-Identify the top websites being visited
-Geolocation reports
-Real-time and historical data
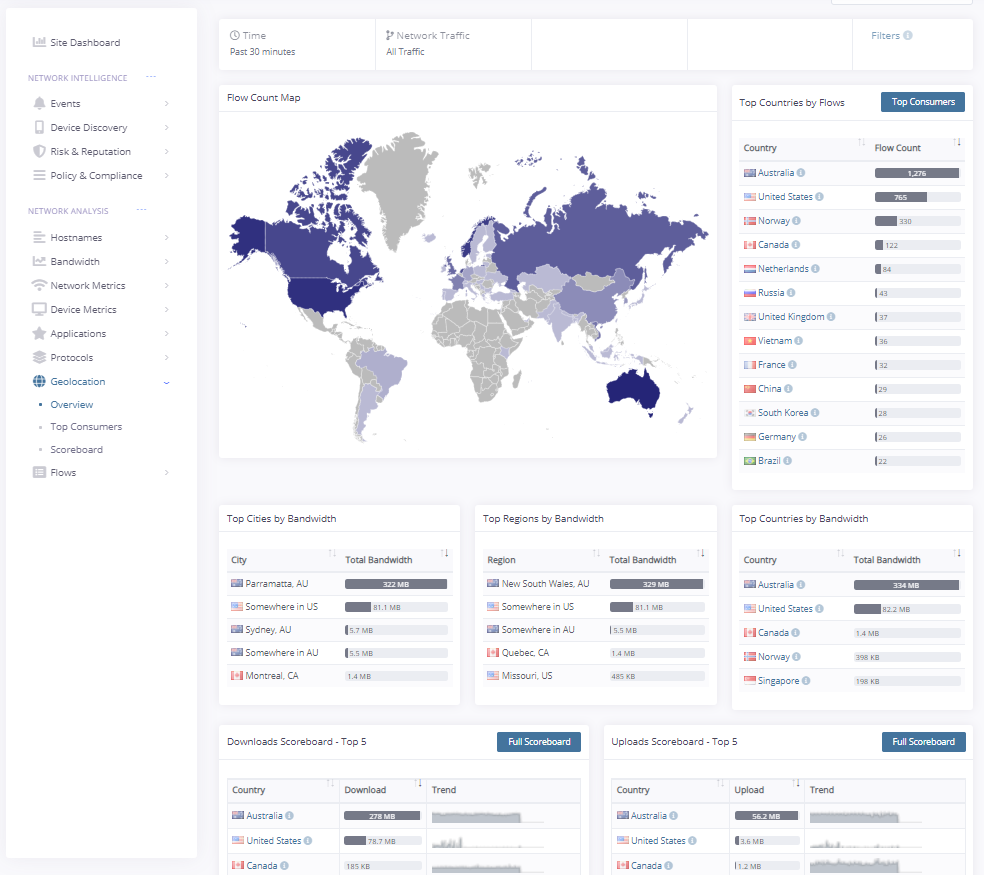
Geolocation
Network geolocation identifies where connections are being made in regions around the world.
-Heat maps quickly show anomalies in typical traffic patterns
-Complement Data Loss Prevention (DLP) techniques
-Track data usage outside boundaries where additional fees may apply
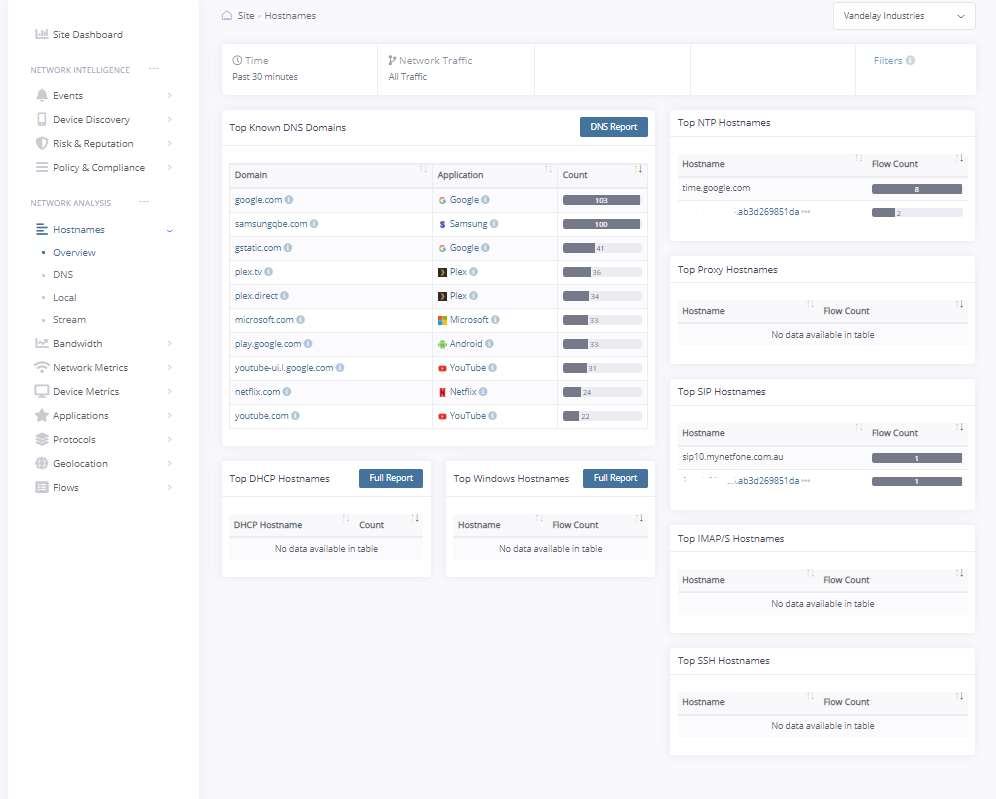
Hostname Visibility
Monitor and record every hostname lookup made by devices on the network.
-View top websites being accessed from within the network
-Identify phishing attempts
-Classify domains by category – technology, news, commerce, social media and more
